OVPN recently launched WireGuard as a VPN protocol in the USA, Gothenburg, Sundsvall and Frankfurt as we are impressed by the VPN protocol and believe that there are several benefits to it. Our deployment will continue over the coming weeks and months until all VPN servers also run WireGuard.
WireGuard often leads to increased speeds and lower latency when using the modern encryption algorithms Curve25519 and ChaCha20.
There are several major differences between WireGuard and the OpenVPN protocol, which OVPN has used since 2014. Some differences are:
- How WireGuard authenticates users
- WireGuard is a newer protocol and still under active development
- Static IP addresses are used in WireGuard instead of dynamic ones
- VPN servers cannot share certificates, (which means load balancing and pool addresses do not work)
Differences between OpenVPN & WireGuard
Let's go through the differences, consequences and what OVPN has done to ensure the integrity of our customers.
How WireGuard authenticates users
OpenVPN can use username and password as an authentication method, but also certificates. OVPN's implementation of OpenVPN uses credentials to authenticate users.
WireGuard uses key pairs, specifically a private key and public key. The private key is private and should never be shared with anyone else, but the public key is what your device uses to authenticate with our VPN servers and can therefore be seen a bit as a username.
The public key is sent to our VPN servers and, in addition to authentication, is also used to encrypt the traffic between your device and the VPN server. Detailed information on this can be found in the WireGuard whitepaper, under the section Cryptokey Routing.
WireGuard is new and still under active development
Until recently, the following appeared on WireGuard's website:
WireGuard is not yet complete. You should not rely on this code. It has not undergone proper degrees of security auditing and the protocol is still subject to change. Still working towards a stable 1.0 release, but that time has not yet come.
The warning has been removed and WireGuard will be included in Linux Kernel 5.6, which is very big news as it is a clear sign that WireGuard is stable and secure.
Static IP addresses are used instead of dynamic ones
At present, WireGuard requires that each key pair (which can be viewed as a device) is assigned a static internal IP address. This works without issues for smaller installations, but can quickly become complex when tens of thousands of customers need to connect. Development is underway for a model called wg-dynamic, but it is not yet finished.
We agree with the WireGuard development team that the usage of static IP addresses is not a big problem as long as it is well managed, or as they write:
Since a server must know each of its clients public keys beforehand, it is not ridiculous to, at the same time, assign a unique link-local IP address to that client.
The VPN servers cannot share certificates
Just as users generate a key pair, so do the VPN servers. Each VPN server has a public key, as well as a private key. The WireGuard configuration files contain the public keys that our VPN servers have.
Since each VPN server needs its own key pair, it is not possible to create a configuration file that can connect to several different VPN servers. Each configuration file can only be used to connect to one specific VPN server which is why the OVPN configuration generator for WireGuard lists all VPN servers separately instead of a single configuration file per region.
WireGuard from an integrity perspective
WireGuard is not built with anonymity in mind. But the same goes for OpenVPN, which is why OVPN made several changes to ensure the integrity of our customers when they connect to our OpenVPN servers.
At present, we are aware of three problems when it comes to WireGuard. There may be more, or new ones may come in the future, as WireGuard is still under active development.
Customers' IP addresses are stored in the VPN server's memory forever
On our VPN servers we can see the following information for connected devices:
peer: W+8RzDtH8PZ970K78BL48xwTq1UlFrNWPo0C7/OFugQ=
endpoint: 217.64.148.10:19223
allowed ips: 172.18.13.3/32, fd00:0:1337:cafe:1111:1111:d4b9:b6dc/128
latest handshake: 17 hours, 31 minutes, 2 seconds ago
transfer: 13.45 MiB received, 62.14 MiB sent
WireGuard associates the customer's IP address (endpoint) with the public key (peer). All VPN protocols do this, otherwise the VPN server would not know where the encrypted packets should be sent. What is different, is that WireGuard does not delete customers' IP addresses when they are no longer active, but this information is stored in the VPN server's memory forever.
To remedy this, we have programmed our VPN servers so that user information is not stored forever in the VPN server's memory. Users who have not had a key exchange for the past three minutes are removed, which means we have as little information as possible:
peer: W+8RzDtH8PZ970K78BL48xwTq1UlFrNWPo0C7/OFugQ=
allowed ips: 172.18.13.3/32, fd00:0:1337:cafe:1111:1111:d4b9:b6dc/128
As a result, OVPN can no longer see when our customers were last connected, or our customers' IP addresses. Our WireGuard VPN servers therefore contain as little information as possible to ensure that WireGuard works.
WireGuard does not assign dynamic IP addresses
As previously mentioned, WireGuard requires that static IP addresses be used.
OVPN has solved this through our WireGuard configuration generator. When keys are generated, or a public key is pasted, we automatically assign an internal static IP address for the key pair. It's possible to see that on the key management tab for your account:
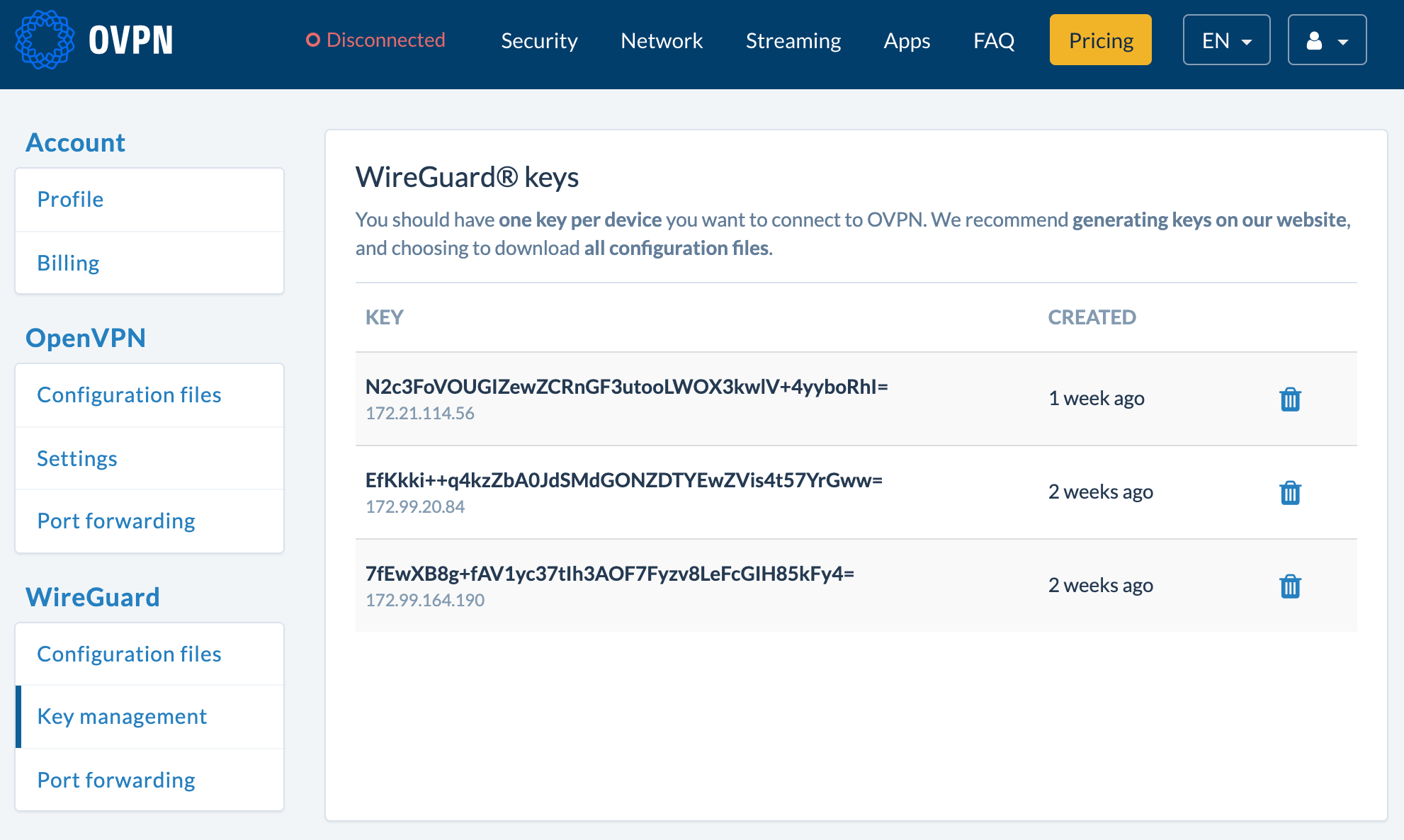
When the configuration files are downloaded, the IP address is included, and it is automatically reserved and sent with the public key to all VPN servers.
Without dynamic IP addresses, users can be traced under certain circumstances
An internal IP address should never be visible on the Internet. However, WebRTC can leak the internal IP address, which is why our browser extension blocks that functionality in WebRTC.
You can test if you have any WebRTC leaks. The WebRTC test is automatically executed every time you visit the dashboard, as well a DNS leak test.
However, if the internal IP address is visible on the Internet, and it never changes, it could under certain circumstances enable the tracking of users.
In addition to blocking WebRTC, it is possible to neutralize the problem by rotating IP addresses. To rotate IP addresses, you currently have to remove the existing WireGuard key from your profile and generate a new key, since you'll also be allocated a new internal IP address.
When WireGuard is integrated into OVPN's custom-built desktop client, we will build in support for rotating keys — and thus also IP addresses — automatically every seven days. Our current forecast is that the WireGuard integration will be ready by summer.
What some VPN providers incorrectly say about WireGuard
OVPN is not the only VPN service running WireGuard, there are a few others as well. Some VPN services have explicitly stated, however, that they will not use WireGuard due to a few things.
Perfect Privacy writes:
WireGuard has no dynamic address management, the client addresses are fixed. That means we would have to register every active device of our customers and assign the static IP addresses on each of our VPN servers. In addition, we would have to store the last login timestamp for each device in order to reclaim unused IP addresses. Our users would then not be able to connect your devices after a few weeks because the addresses would have been reassigned.
They claim that they need to save a timestamp for when each customer was last connected, in order to "recover" IP addresses. We do not understand their reasoning behind this as it is not at all required.
We allocate a random IP address in the range 172.16.0.0/12 to our customers, which means we have about a million possible IP addresses that can be allocated. It is more than enough to meet our needs. No timestamp need to be created at all in order to "reclaim" IP addresses.
VPN.ac mentions:
By design, WireGuard isn’t suitable for none/limited logging policies. Specifically, last public IP of user would be saved on the server used to connect to and it can’t be removed within a day as per our current privacy policy. At a later date we will likely make some tweaks to the source code to sanitize or remove the last used public IP.
The default setting in WireGuard is, as previously mentioned, to save connected IP addresses forever, but this is bypassed by our VPN servers which deletes sensitive information after three minutes for disconnected users.
AirVPN mentions:
Wireguard lacks dynamic IP address management. The client needs to be assigned in advance a pre-defined VPN IP address uniquely linked to its key on each VPN server. The impact on the anonymity layer is catastrophic;
We do not agree that using static IP addresses would be disastrous. As mentioned before, static IP addresses can, in some circumstances, cause users to be traced. Our browser add-on counteracts this at present and our future client will make it even easier for customers to automatically rotate IP addresses and keys.
Summary
By using a VPN service you transfer the trust from your internet provider to your VPN provider (which hopefully is OVPN). It is crucial that you use a VPN service that is reliable, transparent on how the service is run and that can explain what steps have been taken to protect your anonymity and privacy.
We hope this review has been successful in explaining how OVPN ensures the integrity of our customers when they connect to our VPN servers via WireGuard.
WireGuard® is a registered trademark of Jason A. Donenfeld.

